A critical zero-day vulnerability in Microsoft SharePoint Server, CVE-2025-53770, is being actively exploited in targeted attacks against enterprises and government systems. The exploit allows unauthenticated remote code execution (RCE), key theft, and persistent backdoor installation.

Organizations running on-premises SharePoint (Subscription Edition, 2019, and 2016) face immediate operational, legal, and reputational risk if unpatched or misconfigured.
Technical Overview
- CVE IDs: CVE-2025-53770 (primary RCE), CVE-2025-53771 (chained)
- Vulnerability Class: .NET ViewState Deserialization + Path Traversal
- Affected Platforms:
- SharePoint Server Subscription Edition
- SharePoint Server 2019
- SharePoint Server 2016
- Attack Vector: Unauthenticated HTTP(S) request to
ToolPane.aspxleveraging insecure ViewState + malicious path traversal to drop arbitrary code in server-side layouts. - Payload:
spinstall0.aspxweb shell deployed for persistent control and exfiltration.
Technical Implications:
- Machine key compromise: Allows attackers to sign payloads that bypass authentication controls.
- Web shell persistence: Enables long-term command and control (C2) access.
- Post-exploitation lateral movement: Via NTLM relay, LDAP harvesting, or credential dumping.
- Detection challenges: Use of legitimate pages (
ToolPane.aspx) and tampering with AMSI logging
Immediate Remediation Guide
1. Patch All Versions Immediately
-
- Subscription Edition → KB 5002768
- SharePoint 2019 → KB 5002754 AND KB 5002753
- SharePoint 2016 → KB 5002760 (language pack), KB 5002759 (core)
2. Rotate SharePoint Server ASP.NET machine keys
After applying the latest security updates above, it is critical that to rotate SharePoint server ASP.NET machine keys and restart IIS on all SharePoint servers.
To update the machine keys for a web application using PowerShell:
- Generate the machine key in PowerShell using Set-SPMachineKey
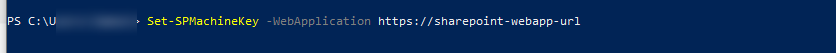
- Deploy the machine key to the farm in PowerShell using Update-SPMachineKey
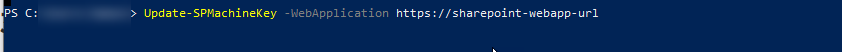
3. IIS “iisreset” reset after the rotation has completed.
iisreset is required to ensure all SharePoint services immediately load the new machine keys from web.config and prevent use of old keys left in memory.
Why Machine Key Rotation matters
- Patching alone is not enough: Attackers who have already stolen validation/decryption keys can continue creating malicious ViewState payloads.
- Microsoft guidance: The Microsoft Defender Vulnerability Management blog recommends rotating the machineKey twice, once before and once after applying patches to ensure complete protection.
- Double rotation: This practice helps eliminate lingering threats and prevents attackers from exploiting stolen cryptographic material.
Summary
- Exploit in-the-wild: The ToolShell exploit (CVE-2025-53770) is actively targeting on-premises SharePoint servers.
- Patches ongoing: Subscription Edition, 2019 and 2016 have patches available
- MachineKey rotation is critical: Machine key rotation is essential to invalidate stolen keys and stop persistent threats.
- Post Rotation: Always restart IIS on all SharePoint servers using
iisreset.exeto apply changes immediately.
For comprehensive information, please refer to Microsoft’s official Common Vulnerabilities and Exposures (CVE) documentation for CVE-2025-53770 and related vulnerabilities
Disclaimer: Always back up your configuration (web.config and other) and test changes in a non-production environment before applying them to live systems.
→ Securing SharePoint Against Current and Future Threats
To protect your SharePoint deployment from this and future threats:
- Maintain Up-to-Date Systems: Ensure all SharePoint servers and related infrastructure are fully patched with the latest Microsoft security updates.
- Rotate Cryptographic Keys Regularly: Periodically rotate machine keys, especially following security incidents to reduce the risk of key compromise.
- Implement Comprehensive Logging and Monitoring: Enable detailed logging for SharePoint, including Antimalware Scan Interface (AMSI) and Windows Event Logs. Monitor for signs of tampering, suspicious activity.
- Apply Network and Access Controls: Restrict access to SharePoint administrative interfaces, especially the Central Administration site and other configuration pages by implementing network segmentation, VPNs, and firewall rules. Ensure that only authorized personnel can reach these sensitive areas by limiting access to trusted networks or through secure remote access solutions.
- Backup and Test Configurations: Regularly back up key configuration files (e.g.,
web.config,machine.config) and test patches and updates in a controlled staging environment prior to production deployment.

